Self-Sovereign Use Case Interaction
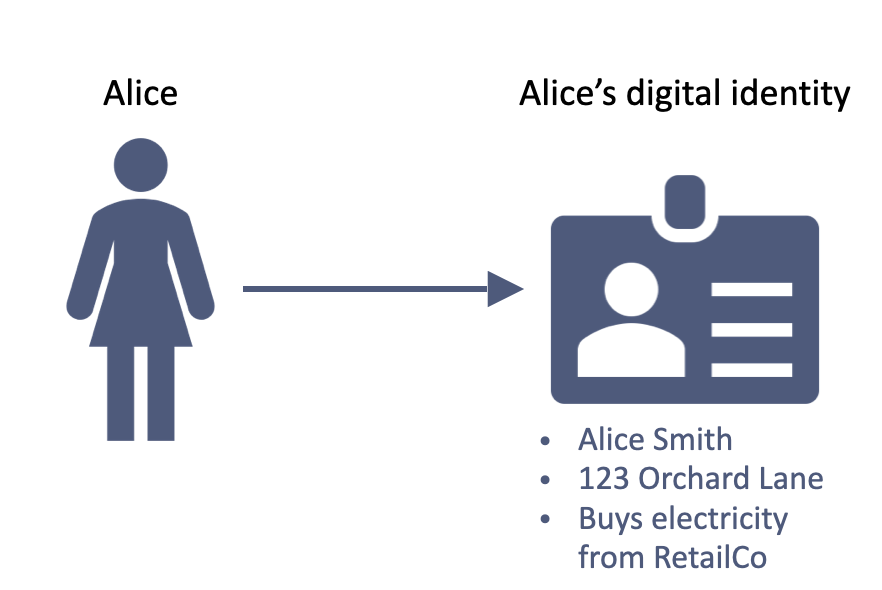
1. Alice creates a digital identity
She can manage her data and consents using a unique, secure digital signature
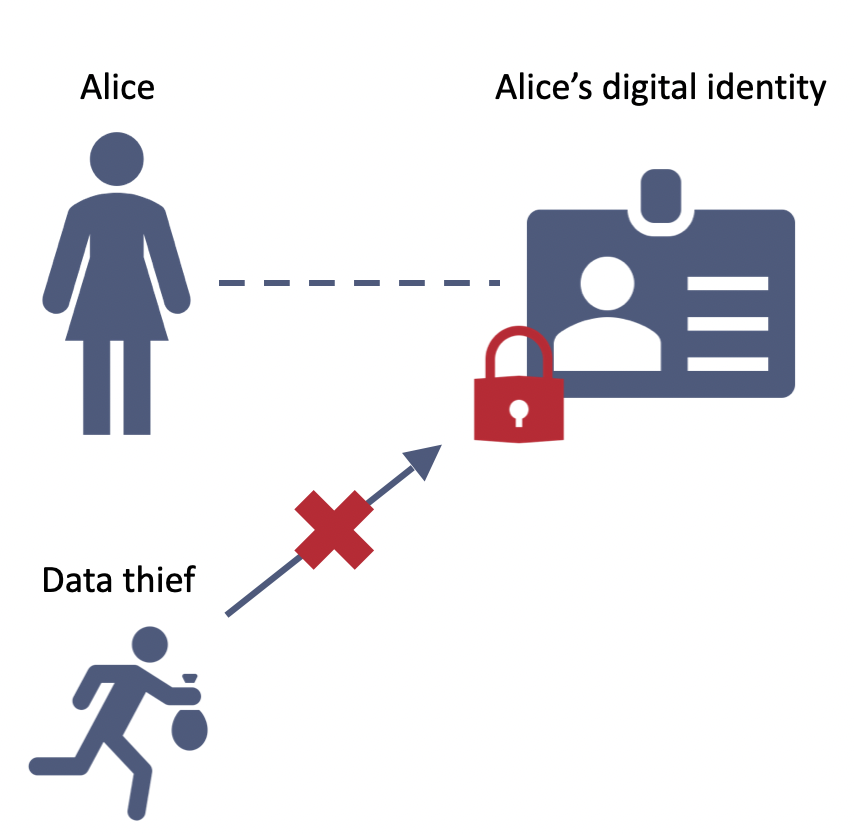
2. The data is encrypted and inaccessible to anyone without Alice’s consent
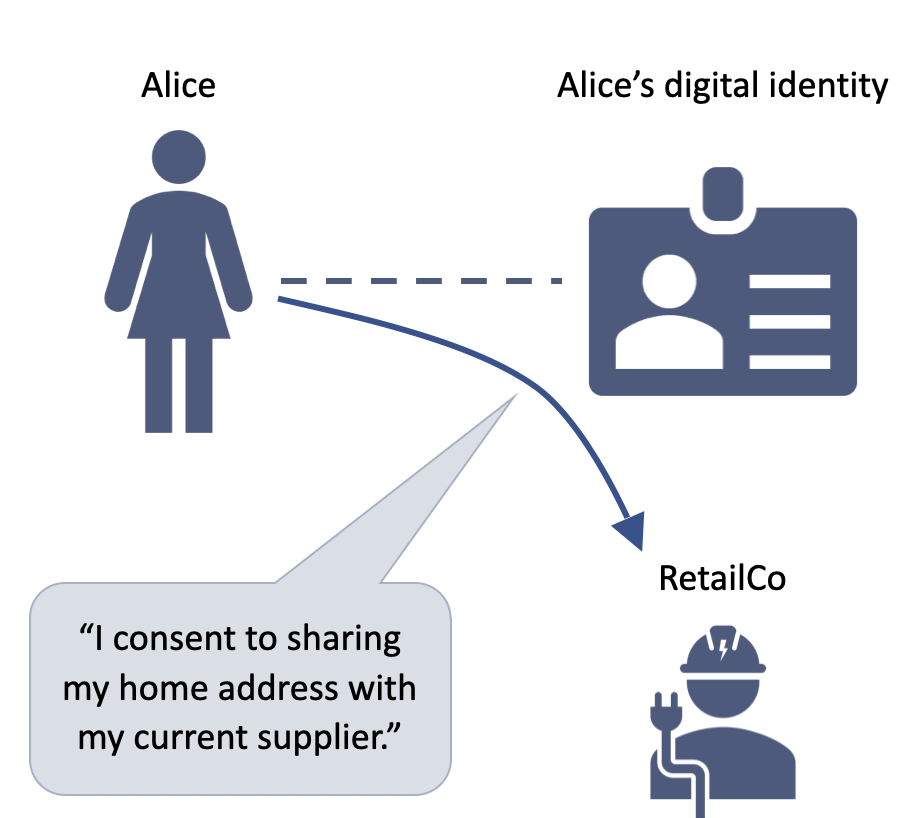
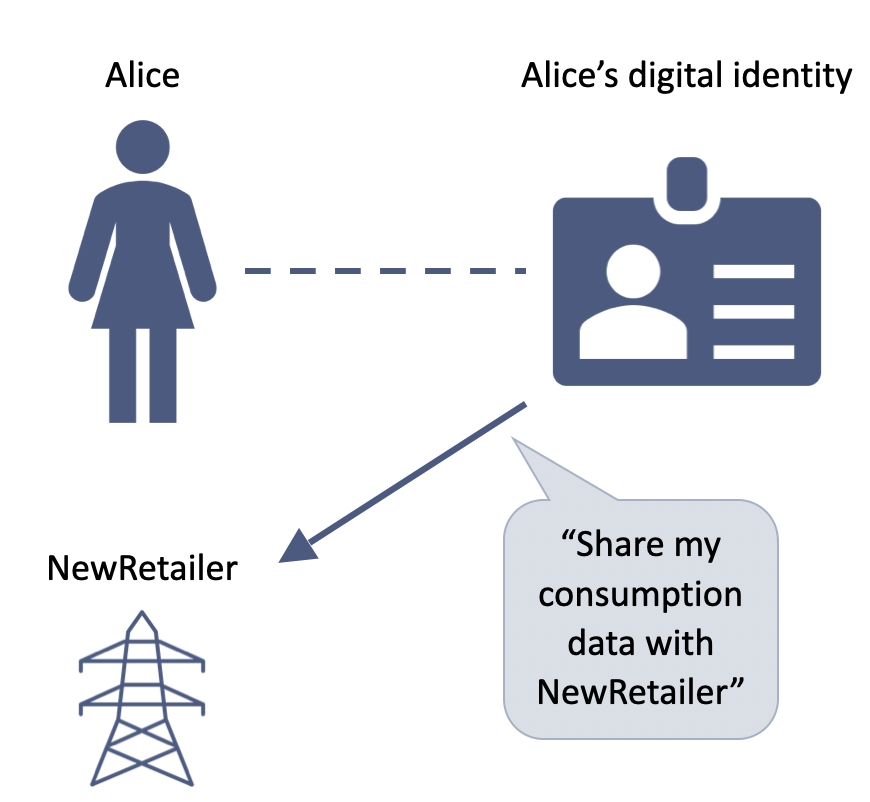
3. Alice can share her data with others
She must explicitly consent to this
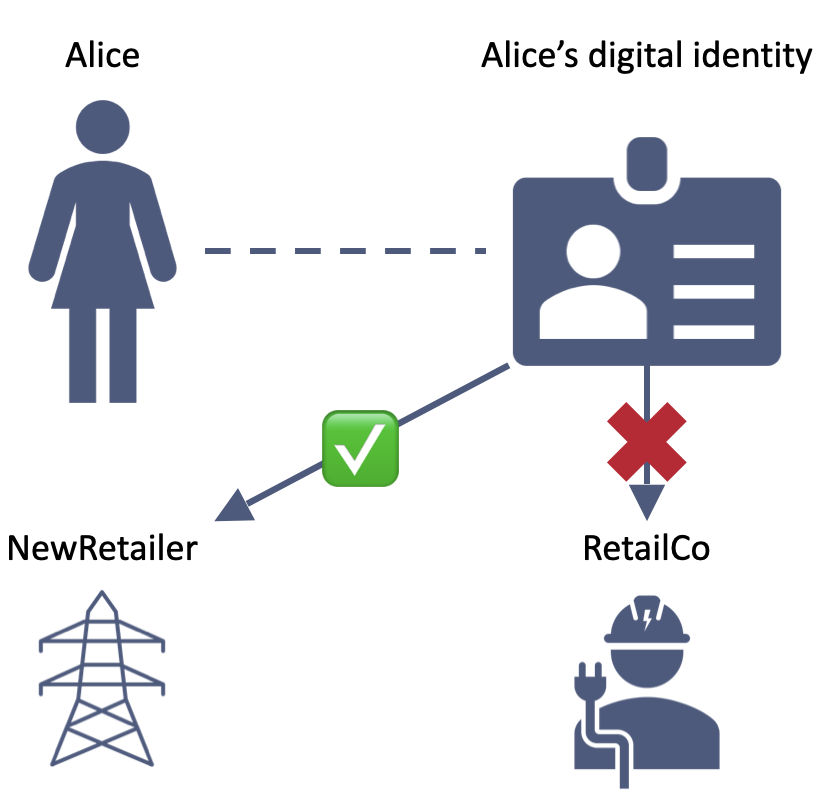
She can revoke her consent at any time
The recipient does not store the data
She can prove or reveal attributes without revealing the entire underlying data
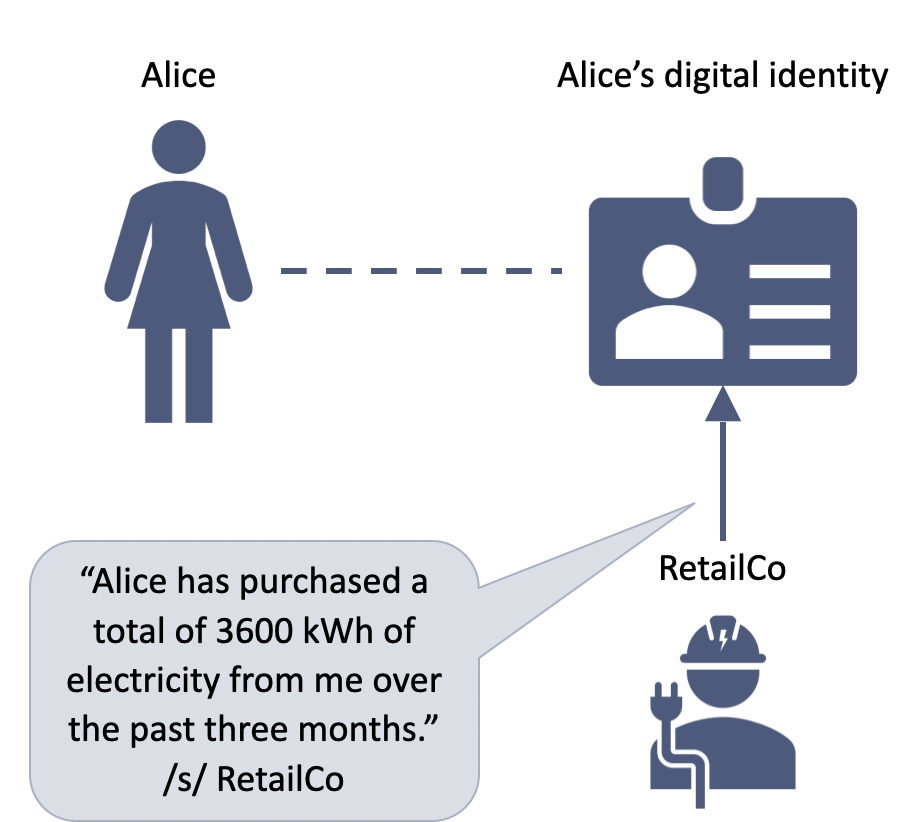
4. Alice can add verified data from others, if she chooses
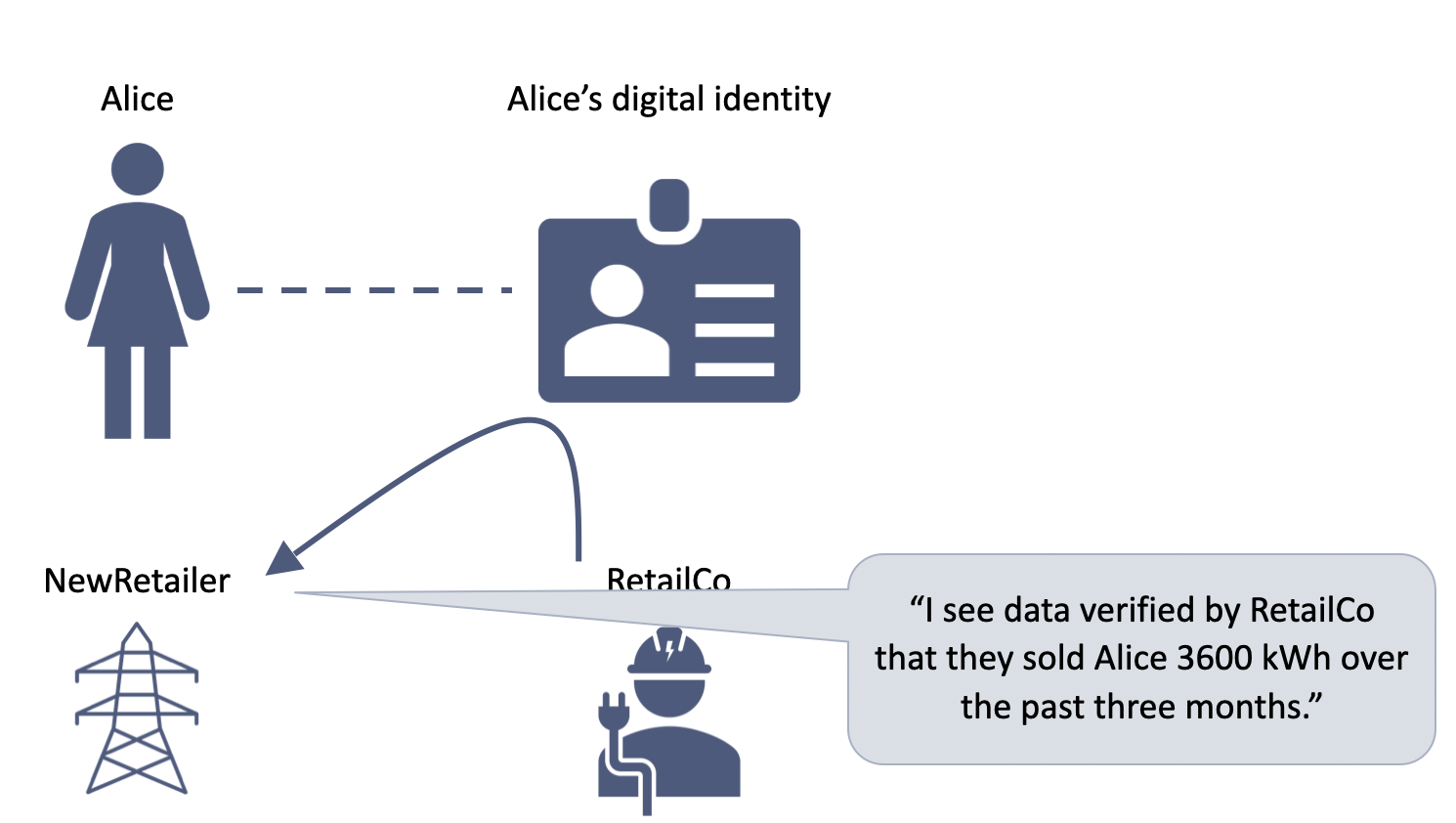
5. Alice can then consent to share that verified data with a third party
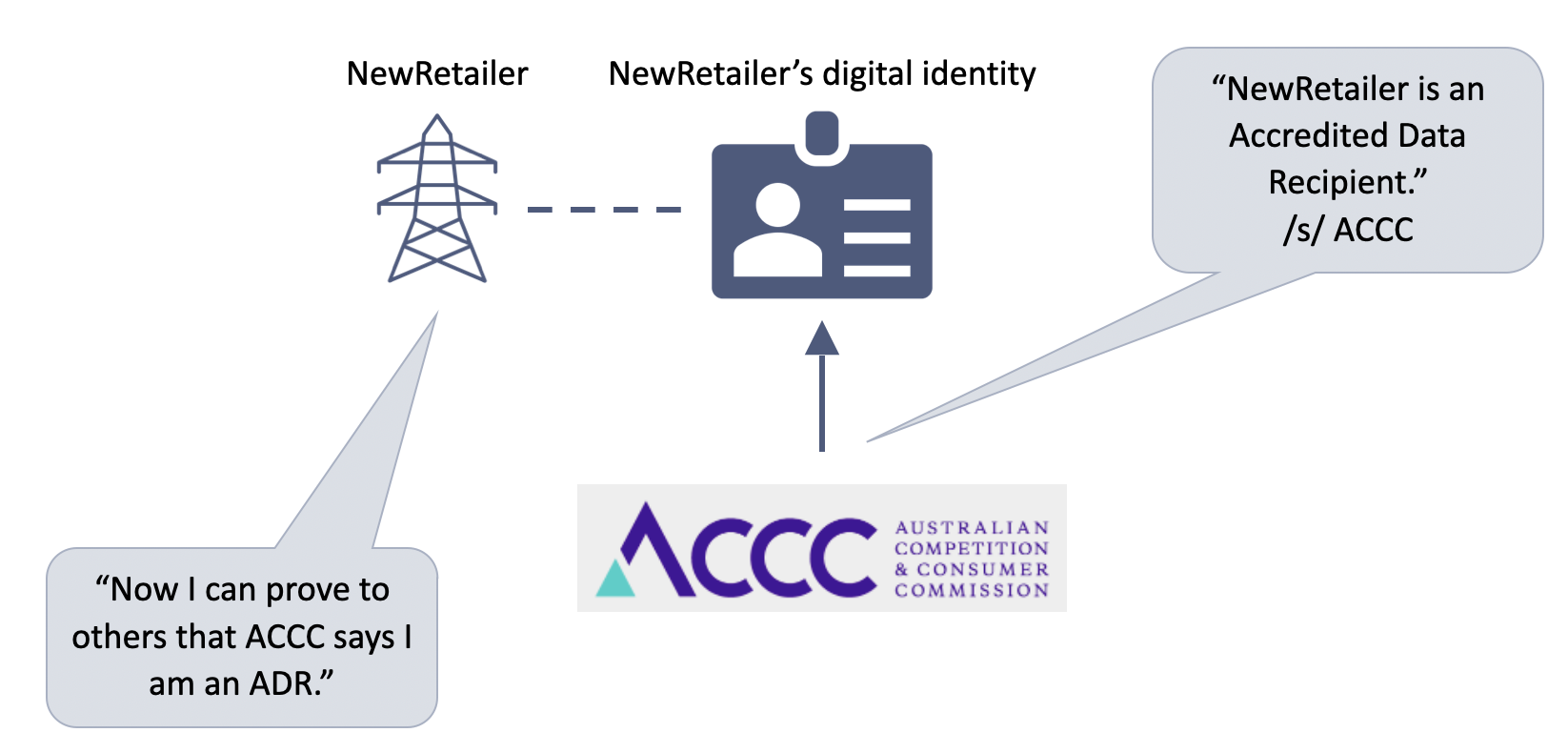
6. The third party can see both the data and its verified source
7. If/when conditions (e.g., contractual relationships) change, Alice modifies her consent to change permissions for ADRs
Alice keeps her digital identity in perpetuity; there is no need to re-register / duplicate digital identities across different systems
This architecture can be applied in any market context and with other types of data
Last updated